| Lesson 6 | Understanding Internet Protocols |
| Objective | Describe protocols. |
Describe Internet Protocol
If the Queen of England visited the President of the United States, there would be a reception full of ambassadors and other politicians at the White House. Who sits where, who introduces who, what people say when they greet the Queen or the President or when they say good bye would follow a strict set of rules that are known as "protocol." These rules (and their order!) are very important in the world of diplomacy. Failing to follow them could actually be taken as an offense and even break relations between countries. Protocol establishes strict order to how things are done, as in the series of diplomatic customs discussed above. And the Internet is not an exception. To be able to send and receive information over the Internet, specific protocols have been developed which dictate precisely the order and method in which it is performed. Internet protocols are easier to master than diplomatic protocols, because their rules are strictly logical.
A protocol is a set of logical rules that define how computers send and receive information, so that two computers can exchange data. There are two types of protocols: 1) proprietary and 2) open. Proprietary protocols are vendor-specific, which are particular to a specific vendor. For example, MS Windows Networking works on Windows based computers, and AppleTalk works on Macintosh computers. Open protocols are published specifications that anyone can use. For example, TCP/IP, HTTP, and FTP work on UNIX, Windows-based computers, and Macintosh computers.
A protocol is a set of logical rules that define how computers send and receive information, so that two computers can exchange data. There are two types of protocols: 1) proprietary and 2) open. Proprietary protocols are vendor-specific, which are particular to a specific vendor. For example, MS Windows Networking works on Windows based computers, and AppleTalk works on Macintosh computers. Open protocols are published specifications that anyone can use. For example, TCP/IP, HTTP, and FTP work on UNIX, Windows-based computers, and Macintosh computers.
Successor Networking Technology to AppleTalk
Apple did not explicitly have a single "successor" to AppleTalk. Instead, it transitioned to a combination of widely adopted networking technologies over time:
- TCP/IP:This became the dominant protocol for general networking, and Apple products gradually shifted to support it fully by the late 1990s and early 2000s. Mac OS X, released in 2001, relied heavily on TCP/IP for networking.
- Ethernet:As Ethernet became the dominant physical layer technology for wired networks, Apple adopted it as the primary means of physically connecting devices.
- Wi-Fi:With the rise of wireless networking, Apple embraced Wi-Fi standards and protocols, allowing its devices to connect to wireless networks.
The Nature of Protocols
Protocols can be either connectionless or connection-oriented. Connectionless protocols do not maintain their connection to the client[1]. After data is transmitted, the client and server disconnect. If the user requested additional information, the client/server connection would have to be reestablished. UDP is an example of a connectionless protocol. A connection-oriented protocol establishes a virtual circuit to begin a conversation and sequences and acknowledges all transmitted data. TCP/IP is also used on intranets inside many companies. TCP[2] is an example of a connection-oriented protocol. After data has been transmitted, the client remains connected to the server. The client must end the session in order to break the connection.
The following series of images illustrates the protocol process:
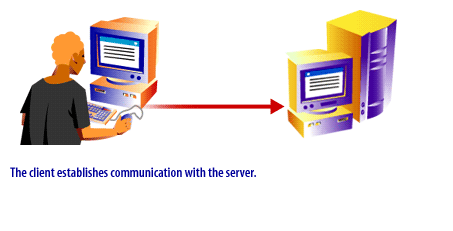
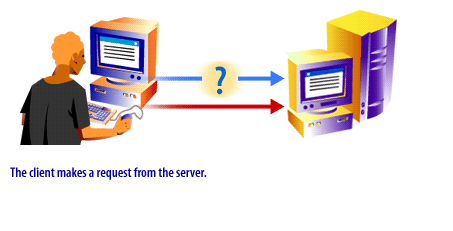
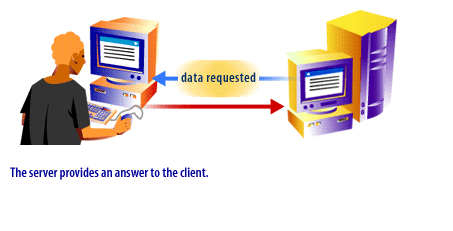
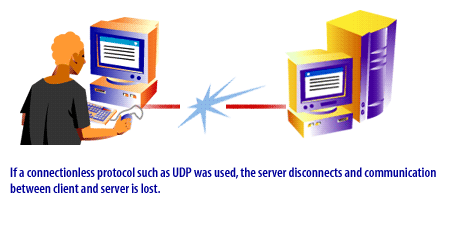
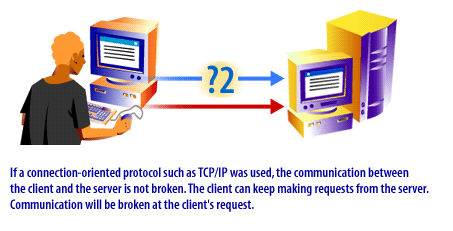
In the next lesson, two particular protocols, UDP and TCP/IP will be discussed.
[1]Clients: A computer (CPU, hard drive, and monitor) configured to receive data on a network. Clients host the browsers that access and display Web resources.
[2]TCP/IP (Transmission Control Protocol/Internet Protocol): One of the main protocols used on the Internet for transferring information from computer to computer.