| Lesson 10 | SSL transactions |
| Objective | Describe the SSL protocol and its use in secure communications. |
SSL Transactions (Secure Communications)
You now understand certificates. Enterprise-grade Web servers allow you to use
certificates for authentication and SSL encryption. The SSL protocol allows applications to exchange data over public networks privately, preventing
eavesdropping, tampering, and message forgery. SSL enables two applications to communicate over the network using authentication with digital
certificates. In addition, message reliability is ensured with SSL's use of encryption and message digests.
When using the SSL protocol, the top-level sequence of events is:
When using the SSL protocol, the top-level sequence of events is:
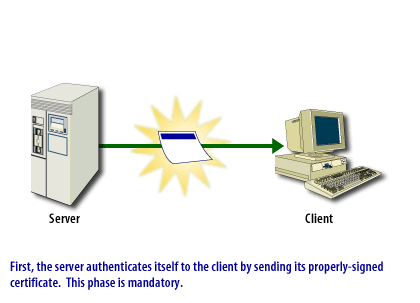
- The client and server applications using the asymmetric keys in the form of certificates are authenticated.
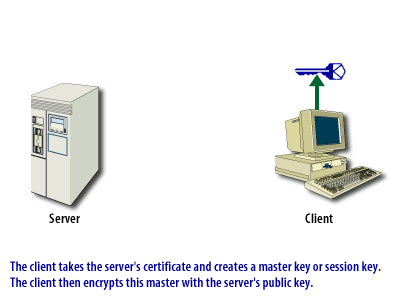
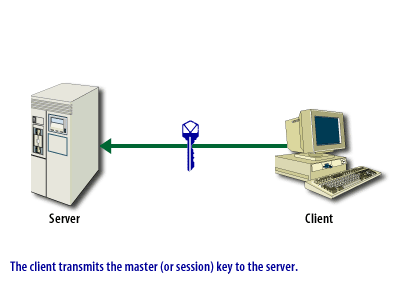
- A random symmetric session key is encrypted to the server's public key and transmitted to the server.
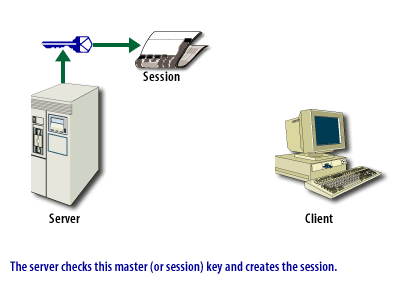
- All data is encrypted using the random symmetric key.
- A message authentication that has an algorithm is applied to envelop all information to ensure integrity.
(SSL) Secure Socket Layer
The Secure Sockets Layer (SSL) protocol plays a pivotal role in securing communications for ecommerce by establishing an encrypted link between two parties, typically
Once the handshake is complete, all data that flows between the client and server is encrypted using symmetric encryption, where both parties use the same key to encrypt and decrypt messages. This key exchange is secured by the asymmetric encryption method used during the handshake, leveraging the public and private key pair. In the context of ecommerce, this encryption is crucial for safeguarding sensitive details like credit card numbers during transactions. SSL also ensures data integrity through mechanisms like message authentication codes (MAC), which detect any tampering or corruption of data in transit, thus providing an additional layer of security against man-in-the-middle attacks where an attacker might attempt to intercept or alter the communication.
Moreover, SSL contributes to the establishment of trust in ecommerce by providing visible indicators of security to users. When an SSL certificate is properly implemented, web browsers display security cues like a padlock icon or a green address bar (for Extended Validation certificates), signaling to consumers that their connection is secure. This visibility not only reassures customers about the safety of their transactions but also helps in building the reputation of the ecommerce site as trustworthy. Compliance with SSL standards can also be a requirement for various payment gateways and for adhering to regulations like PCI DSS (Payment Card Industry Data Security Standard), which mandates secure transmission of cardholder data, thereby making SSL an indispensable component of the ecommerce security framework.
SSL encrypts communications between two points. It is not as ambitious as SET, which outlines a more ambitious information exchange procedure in addition to encryption. Although SSL helps prevent eavesdropping from hackers, it is not completely secure. Most nations have embraced the use of SSL, but e-commerce will likely move to protocols such as SET or radically improved uses of SSL to ensure that customers feel completely secure about transacting online. The following series of images demonstrates the latest in SSL protocol technologies
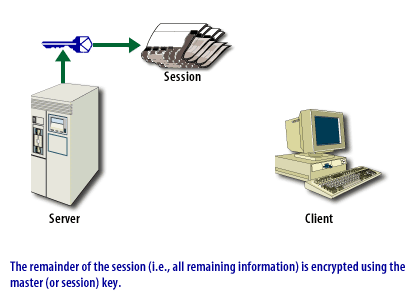
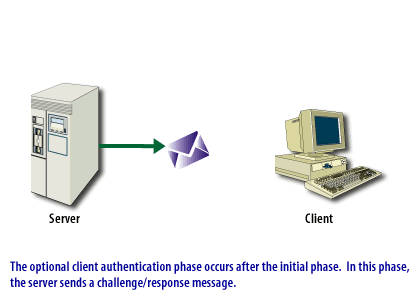
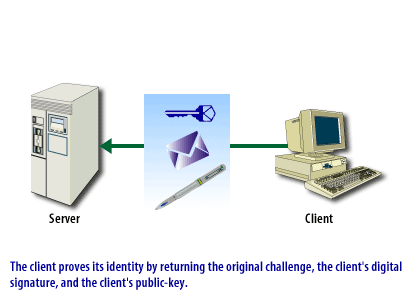
An SSL connection can be in two phases, as shown in the ssl-connection below.
- a web server (the ecommerce site) and
- a web browser (the customer).
Once the handshake is complete, all data that flows between the client and server is encrypted using symmetric encryption, where both parties use the same key to encrypt and decrypt messages. This key exchange is secured by the asymmetric encryption method used during the handshake, leveraging the public and private key pair. In the context of ecommerce, this encryption is crucial for safeguarding sensitive details like credit card numbers during transactions. SSL also ensures data integrity through mechanisms like message authentication codes (MAC), which detect any tampering or corruption of data in transit, thus providing an additional layer of security against man-in-the-middle attacks where an attacker might attempt to intercept or alter the communication.
Moreover, SSL contributes to the establishment of trust in ecommerce by providing visible indicators of security to users. When an SSL certificate is properly implemented, web browsers display security cues like a padlock icon or a green address bar (for Extended Validation certificates), signaling to consumers that their connection is secure. This visibility not only reassures customers about the safety of their transactions but also helps in building the reputation of the ecommerce site as trustworthy. Compliance with SSL standards can also be a requirement for various payment gateways and for adhering to regulations like PCI DSS (Payment Card Industry Data Security Standard), which mandates secure transmission of cardholder data, thereby making SSL an indispensable component of the ecommerce security framework.
SSL encrypts communications between two points. It is not as ambitious as SET, which outlines a more ambitious information exchange procedure in addition to encryption. Although SSL helps prevent eavesdropping from hackers, it is not completely secure. Most nations have embraced the use of SSL, but e-commerce will likely move to protocols such as SET or radically improved uses of SSL to ensure that customers feel completely secure about transacting online. The following series of images demonstrates the latest in SSL protocol technologies
An SSL connection can be in two phases, as shown in the ssl-connection below.
SSL Connection
- For more information about SSL, go to www.ssl.com.
- For more information about cryptography in general, go to rsa.com