| Lesson 7 | E-commerce and encryption |
| Objective | Define encryption methods and types. |
e-commerce and Encryption
Cryptographic methods form the foundation of all e-commerce transactions. For the purposes of e-commerce, applied cryptography is the study of the process of creating cipher text (encrypted text) from plain text (human readable text). The types of encryption relevant to e-commerce are listed in the table below.
| Encryption type | Description | Common algorithms and uses |
| Symmetric key | Uses a single key to encrypt and decrypt data. | DES, Triple DES, RC2; used for encrypting large amounts of data. |
| Asymmetric key | Uses a mathematically related public/private key pair; also known as public key encryption. | RSA enables secure key exchange. Diffie/Hellman explains the concept of key exchange. |
| One way | A one way encryption algorithm produces ciphertext that cannot be taken BACK to the original plaintext. | Used for signing data and transactions. |
| Hash function | A smaller numerical representation of the plaintext. | A hash of a message is encrypted using one way encryption to become the signature for that message. |
| Applied encryption | Uses a combination of symmetric, asymmetric, and one-way encryption for enhanced security. | Email, credit card encoding, S/MIME and SSL protocols, SETs, payment gateways. |
Using encryption in e-commerce
Symmetric encryption[1] is necessary because it encrypts data quickly and it is relatively secure. However, it is very difficult to distribute the symmetric keys securely in an e-commerce setting. Because the same key both encrypts and decrypts the data, you must keep the key secret. Yet, how do you get this key to its destination once you have encrypted the message? Asymmetric encryption[2] handles this process, because it is able to use a key pair, where one key is made freely available and the other remains completely private. For example, an email program uses symmetric encryption to encrypt the actual data. It uses asymmetric encryption to encrypt symmetric keys. It then uses one-way encryption to sign the data to ensure that the information has not been tampered with.
This is all encrypted to the receiver's public key, then sent across the network wire. When the receiver gets the message, the receiver uses the private key (the second half of the key pair) to decrypt the asymmetric encryption. The receiving computer decrypts the text with the symmetric key, then calculates the hash value. If the hash value is correct, the message has not been tampered with, and the email browser that supports these protocols allows the message to be read.
- Challenges of implementing Encryption for e-commerce Transactions
Implementing encryption for e-commerce transactions is critical for ensuring data security, maintaining user trust, and adhering to regulatory compliance. However, encryption implementation does present a set of challenges:- Complexity of Setup and Maintenance: Setting up a robust encryption system requires careful selection of the right encryption algorithms, generation of secure keys, and the establishment of a key management process. Maintaining this system, including periodic updates and vulnerability checks, adds layers of complexity that businesses need to manage.
- Performance Overhead: Encryption and decryption processes, especially with strong cryptographic algorithms, consume computational resources. This can introduce latency into the transaction process, potentially affecting user experience, especially during high-traffic periods.
- Key Management: Effective management of cryptographic keys, including generation, distribution, rotation, and disposal, is crucial. Mishandling or misplacing encryption keys can lead to data breaches or loss of access to encrypted data, both of which have dire consequences.
- Compliance and Regulatory Landscape: Different jurisdictions and industries have distinct regulations concerning data protection and encryption standards. Navigating this complex landscape and ensuring compliance can be challenging for businesses that operate internationally.
- Cost Implications: Implementing robust encryption solutions can be expensive, especially for small to medium-sized businesses. Costs not only involve the initial setup but also ongoing maintenance, training, and potential updates.
- Interoperability Issues: Different e-commerce platforms, payment gateways, and service providers may employ varied encryption standards and methods. Ensuring consistent encryption and seamless interoperability across all these components can be challenging.
- User Experience Concerns: While encryption secures data, additional authentication steps or minor delays due to the encryption process can sometimes inconvenience users. Striking a balance between security and user experience is essential.
- Potential for Human Error: Even with the most secure encryption methods, human errors, such as weak password practices or mishandling of encrypted data, can introduce vulnerabilities.
- Emerging Threats: With the rapid evolution of cyber threats and the advent of quantum computing, there's a need to continually monitor and update encryption methods to counteract these advanced threats.
- Vendor Lock-in: Businesses often rely on third-party solutions for encryption. Transitioning between these solutions, or attempting to integrate multiple solutions, can introduce challenges, especially if there's a lack of standardization.
While encryption is indispensable for securing e-commerce transactions, businesses must be cognizant of the associated challenges. Through proactive planning, continuous monitoring, and leveraging expertise, these challenges can be effectively addressed, ensuring both security and operational efficiency.
The following series of images below describes how this process works.
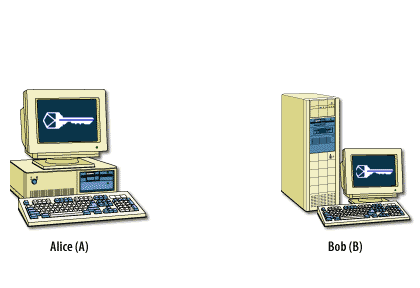
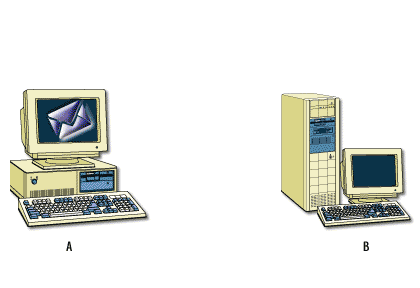
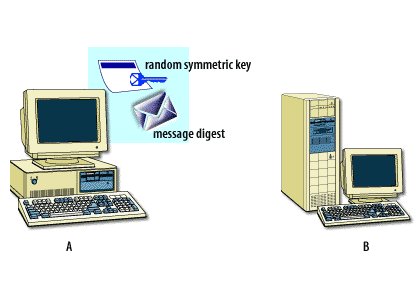
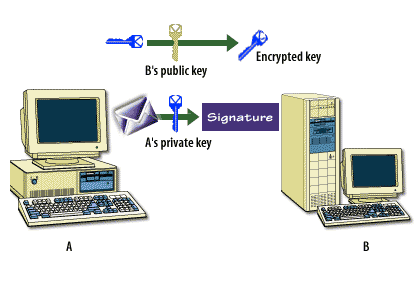
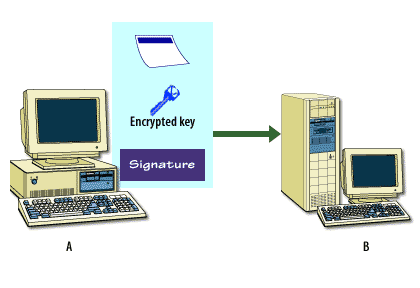
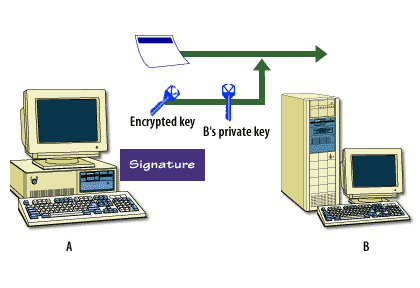
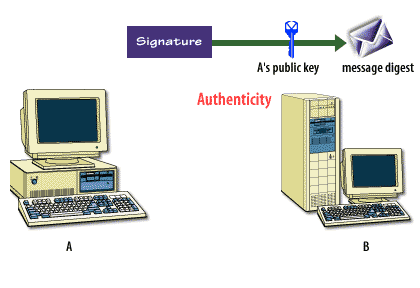
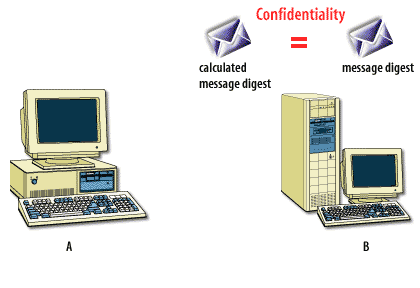
Encryption and Certificates
The defense-in-depth strategy toward security requires system administrators to
take every possible action to improve security. One significant improvement to security can be obtained by widespread use of encryption. With respect to the
UNIX workstation, the following are security advantages to be gained:
- If a workstation gets compromised and taken over by an attacker, previously encrypted files are likely to be protected. This assumes that passphrases used to encrypt the data are kept in the users memory and not on the workstation.
- By encrypting traffic on the local area network (LAN), the risk of being attacked from a local source is greatly reduced. Many organizations consider their biggest security feature to be the firewall between the LAN and the Internet. Hower, other workstations on the LAN also pose a significant threat. For example, if the LAN is hubbed, any workstation can listen in on all instant messaging to and from another worksation. Even if the network is switched there are readily available tools, such as ettercap, that can monitor all traffic in and out of a workstation.
- Much of the traffic that travels over the Internet, such as e-mail or FTP, is in the clear or unencrypted. The only protection afforded to this traffic is security through obscurity. In other words, the telnet, e-mail, and FTP traffic can be read in many places as the traffic is routed, but who would want to? Most users would not find this level of security very comforting.
Cyber Security Management
You will learn about security services in the next lesson.
[1]Symmetric encryption: Encryption that uses the same key to encrypt and decrypt information.
[2]Asymmetric encryption: Encryption that creates a public key and a private key. The private key remains secret, on your computer. You can freely disseminate the public key.