| Lesson 8 | Security Services |
| Objective | Describe the Application of Encryption Methods to Security Services. |
Application of Encryption Methods
Email, virtual private network (VPN) connections, and other forms of enterprise-grade encryption use symmetric, asymmetric, and one-way encryption all at once.
The various encryption methods enable you to achieve:
The following image below describes these security services.
- Data confidentiality
- Data integrity
- Authentication
- Access control
- Nonrepudiation
The following image below describes these security services.
- Security Services in ecommerce
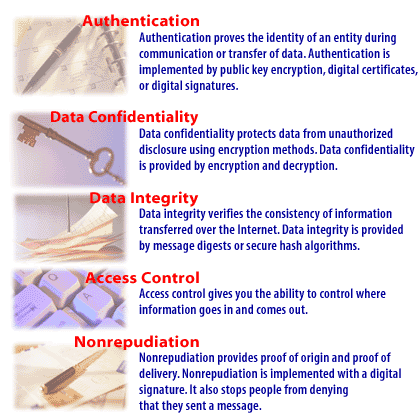
- Authentication: Authentication proves the identity of an entity during communication or transfer of data. Authentication is implemented by public key encryption, digital certificates or digital signatures.
- Data Confidentiality: Data confidentiality protects data from unauthorized disclosure using encryption methods. Data confidentiality is provided by encryption and decryption
- Data Integrity: Data Integrity verifies the consistency of information transferred over the internet. Data integrity is provided by message digest or secure hash algorithms
- Access Control: Access control gives you the ability to control where information goes in and comes out.
- Non-repudiation: Non repudiation provides proof of origin and proof of delivery. Non-repudiation is implemented with a digital signature. It also stops people from denying that they sent a message.
What is a Secure System
A secure system accomplishes its task with no unintended side effects. Using the analogy of a house to represent the system, you decide to carve out a piece of your front door to give your animals easy access to the outdoors. On the other hand, if the hole is too large, burglars may get access. You have created an unintended implication and therefore, an insecure system. In the software industry, security has two different perspectives. In the software development community, it describes the security features of a system. Common security features are ensuring passwords that are at least six characters long and encryption of sensitive data.
For software consumers, it is protection against attacks rather than specific features of the system. Your house may have the latest alarm system and windows with bars, but if you leave your doors unlocked, despite the number of security features your system has, it is still insecure. Hence, security is not a number of features, but a system process. The weakest link in the chain determines the security of the system. In this article, we focus on possible attack scenarios in an e-Commerce system and provide preventive strategies, including security features, that you can implement. Security has three main concepts: confidentiality, integrity, and availability. Confidentiality allows only authorized parties to read protected information. For example, if the postman reads your mail, this is a breach of your privacy. Integrity ensures data remains as is from the sender to the receiver. If someone added an extra bill to the envelope, which contained your credit card bill, he has violated the integrity of the mail. Availability ensures you have access and are authorized to resources. If the post office destroys your mail or the postman takes one year to deliver your mail, he has impacted the availability of your mail.
- Data Security in the Quantum Age
When you drill down in the world of quantum computing, you are confronted with a world that is not based on classical mechanics. The concept itself upsets the calculator that is generally believed to underscore reality. However, there appears to be a deeper, more fundamental, and stranger layer to existence. In the atomic or subatomic realm, particles have been observed that are behaving in a way that conflicts with the physical laws as they have been traditionally defined, thus Einstein's famous description: "spooky action at a distance." From a computing standpoint, if a bit of data is either a 1 or a 0 in a classic computer, that same bit can be simultaneously a 1 and a 0 in the theoretical quantum computer. When very smart people build upon that revolutionary insight, they are naturally excited about the potential commercial applications of quantum computing. The most obvious application is in massively expanding the data-crunching capabilities of the worldwide digital ecosystem. As the data processing boundariesfor the Internet, cell phones, and payment systems continue to be pushed back, the demand for more processing power and speed only grows. Quantum computing has been touted as a solution to this demand. It might be a tad hyperbolic when scientists claim it would take a classic computer the size of the universe to perform as many computations as a single quantum computer, but it is the thought that counts.
Access control
Access control designates the resources a user or service may access on the system or network. Access controls include valid IDs and passwords to control access to system resources. Controls on FTP include when the services can be accessed and by whom (by user or host name). Similarly, HTTP and email have access control restrictions.
- e-commerce Protocols
- Secure MIME (S/MIME): A specification for secure electronic mail. S/MIME was designed to add security to email messages in MIME format. The security services offered are authentication (using digital signatures) and privacy (using encryption). S/MIME assumes that both the sender and receiver of secure email messages have public/private key pairs and uses the concept of a digital envelope
- Secure Sockets Layer (SSL): An encryption method enabled by digital certificates.
- Secure Electronic Transaction (SET): A method of information exchange that allows businesses and clients an extra level of protection while conducting business.
The primary protocols used in e-commerce are the Secure MIME (S/MIME), Secure Sockets Layer (SSL), and Secure Electronic Transactions (SET) protocols. These protocols are discussed in more detail in later lessons. - Encryption Purposes and Methods
- Symmetric: Uses one key to encrypt and decrypt information
- Asymmetric: Uses one key pair to encrypt and decrypt information
- One way: Creates hash code
- Applied: Combines several different encryption strategies
- Data confidentiality: Uses algorithms that make information remain secret
- Data integrity: A service for ensuring that information cannot be altered
- Authentication: Establishes a person's identity
- Access Control: Determines where a person or network host is allowed to enter
- Nonrepudiation: The ability to prove a transaction has in fact occurred
e-commerce System Security
Three Different encryption Methods
There are three different basic encryption methods, each with their own advantages:
Any of these methods would likely prove sufficient for proper data security, and a quick search will reveal the multitude of solutions available for data encryption. Data encryption is a necessity (both for legal reasons and otherwise) when transmitting information like PHI, so no matter what method you choose, make sure you are doing everything you can to protect data. The next lesson concludes this module.
- Hashing: Hashing creates a unique, fixed-length signature for a message or data set. Each hash is unique to a specific message, so minor changes to that message would be easy to track. Once data is encrypted using hashing, it cannot be reversed or deciphered. Hashing, then, though not technically an encryption method as such, is still useful for proving data has not been tampered with.
- Symmetric methods: Symmetric encryption is also known as private-key cryptography, and is called so because the key used to encrypt and decrypt the message must remain secure, because anyone with access to it can decrypt the data. Using this method, a sender encrypts the data with one key, sends the data (the ciphertext) and then the receiver uses the key to decrypt the data.
- Asymmetric methods: Asymmetric encryption, or public-key cryptography, is different than the previous method because it uses two keys for encryption or decryption (it has the potential to be more secure as such). With this method, a public key is freely available to everyone and is used to encrypt messages, and a different, private key is used by the recipient to decrypt messages.
Any of these methods would likely prove sufficient for proper data security, and a quick search will reveal the multitude of solutions available for data encryption. Data encryption is a necessity (both for legal reasons and otherwise) when transmitting information like PHI, so no matter what method you choose, make sure you are doing everything you can to protect data. The next lesson concludes this module.
Security Services - Exercise
Click the Exercise link below to solve a security issue for the course project.
Security Services - Exercise
Security Services - Exercise