Network Security Threats
Worms, Trojan horses, and denial of service types of attacks are utilized maliciously to destroy and consume the given resources of a network .
At times, incorrectly configured hosts and accompanying servers act like threats to network security, since they do eat up available resources without cause.
To be capable of correctly identifying and mitigating such potential threats, an organization has to be ready with the proper security protocols and tools to do the job. A number of the most efficient means for finding and eliminating these types of threats are explored below.
To be capable of correctly identifying and mitigating such potential threats, an organization has to be ready with the proper security protocols and tools to do the job. A number of the most efficient means for finding and eliminating these types of threats are explored below.
Kinds of Different Network Threats
Logic Attacks
The majority of security professionals group the various threats to network security in one of two significant categories.
Either they are
There are cyber criminals who exploit this attack with the intention of willfully gaining illegal access to the system, or downgrading the performance of a given network.
An example of such a threat to network security concerns the notorious ping of death. In this vile attack, the perpetrator dispatches ICMP packets off to a system which will be greater in size than the maximum allowed capacity.
The majority of these sorts of assaults are simply avoided by upgrading software which proves to be vulnerable or by filtering out particular packet sequences.
Either they are
- logic attacks
- or resource attacks.
There are cyber criminals who exploit this attack with the intention of willfully gaining illegal access to the system, or downgrading the performance of a given network.
An example of such a threat to network security concerns the notorious ping of death. In this vile attack, the perpetrator dispatches ICMP packets off to a system which will be greater in size than the maximum allowed capacity.
The majority of these sorts of assaults are simply avoided by upgrading software which proves to be vulnerable or by filtering out particular packet sequences.
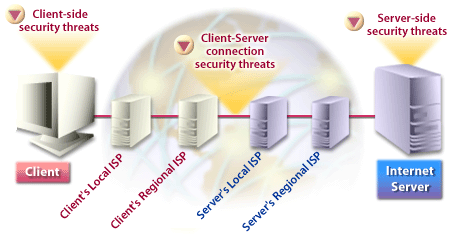
- Security threats on a client system target active content and privacy infringement. In other words, your personal computer system becomes the object of attack.
- Security threats on a server system include server/LAN break-ins, and Denail-of-service attacks.
- Threats to both client and server via the connection between them include eavesdropping and internet fraud.