| Lesson 7 | Auditing |
| Objective | Describe how log files help detect security breaches. |
Log Files detect Security Breaches
Here's how log files play a crucial role in detecting security breaches on an ecommerce website:
🔍 What Are Log Files?
Log files are detailed, time-stamped records of events that happen on your website, server, application, database, and firewall. They capture everything from user logins to failed transactions, page requests, and system errors.
🛡️ How Log Files Help Detect Security Breaches
🧰 Tools That Make Log Analysis Easier
🎯 Final Word: For an ecommerce site, log files are like security cameras", they may not stop a breach by themselves, but they help you see what happened, when, how, and who did it. By monitoring logs effectively, you can detect attacks early, respond quickly, and prevent data loss or financial fraud.
🔍 What Are Log Files?
Log files are detailed, time-stamped records of events that happen on your website, server, application, database, and firewall. They capture everything from user logins to failed transactions, page requests, and system errors.
🛡️ How Log Files Help Detect Security Breaches
-
Unusual Login Patterns
- What to watch for:
- Multiple failed login attempts (brute-force attacks).
- Logins from suspicious IP addresses or unusual geographic locations.
- Log Type: Web server logs, application logs, authentication logs.
- What to watch for:
-
Access to Sensitive Endpoints
- What to watch for:
- Requests to
/admin,/wp-login.php,/login,/cart/checkoutby unauthorized users. - Repeated attempts to access restricted areas.
- Requests to
- Log Type: Web server logs (e.g., NGINX, Apache).
- What to watch for:
-
SQL Injection or Code Injection Attempts
- What to watch for:
- Strange query strings like
?id=1' OR '1'='1or script tags in form fields.
- Strange query strings like
- Log Type: Application logs, database logs.
- What to watch for:
-
Traffic Spikes or Bot Activity
- What to watch for:
- Sudden spikes in traffic to specific product pages or checkout pages.
- Bots scraping pricing or launching denial-of-service (DoS) attacks.
- Log Type: CDN logs, access logs.
- What to watch for:
-
Unexpected File Modifications
- What to watch for:
- Changes to
.php,.js, or config files outside of normal deployment.
- Changes to
- Log Type: System logs, file integrity monitoring logs.
- What to watch for:
-
Suspicious Payment Activity
- What to watch for:
- Multiple failed payment attempts with different credit card numbers.
- High-value transactions from new or unverified accounts.
- Log Type: Payment gateway logs, application logs.
- What to watch for:
🧰 Tools That Make Log Analysis Easier
-
SIEM tools (Security Information and Event Management):
- Splunk
- LogRhythm
- ELK Stack (Elasticsearch, Logstash, Kibana)
- Real-time alerts: Configure alerts when suspicious patterns are detected.
- Log rotation and retention: Keep logs for enough time to identify long-term threats.
🎯 Final Word: For an ecommerce site, log files are like security cameras", they may not stop a breach by themselves, but they help you see what happened, when, how, and who did it. By monitoring logs effectively, you can detect attacks early, respond quickly, and prevent data loss or financial fraud.
Auditing Log Files
You can take a more proactive approach to system security by monitoring the system access and keeping logs on activity conducted to detect security problems and ensure that only authorized users have access.
This is called network auditing. Many utilities are now available to system administrators that detect intruders and perform additional system and network monitoring functions. When selecting network auditing
software, activity logs should be examined for the following:
In the next lesson, you will learn how user and server authentication is used to provide network security.
- Attempts at unauthorized access (failed logins)
- File access attempts and denials
- Attempts to change the permissions settings on a file
- Attempts to change the log
In the next lesson, you will learn how user and server authentication is used to provide network security.
Computer and Internet Security
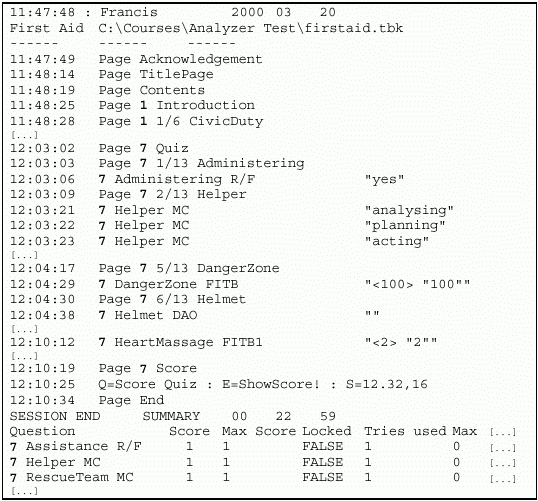
🧠 Context and Overview
- Timestamp Start:
11:47:48 - User: Francis
- Date: March 20, 2000
- Course:
C:\Courses\Analyzer Test\firstaid.tbk - The log records the user's navigation, quiz interactions, and responses within the First Aid training application.
📄 Sections of the Log
-
Navigation and Page Views
- Each line includes a timestamp, page info, and sometimes a quiz question:
-
11:48:19 Page TitlePage 11:48:25 Page 1 Introduction 12:02:03 Page 7 Quiz
-
Quiz Interactions
- The user interacts with quizzes and responds to various types of questions:
-
- R/F (Right/False): e.g.,
Administering R/F "yes" - MC (Multiple Choice): e.g.,
Helper MC "analysing","planning","acting" - DAO (Drag and Order?): e.g.,
Helmet DAO "" - FITB (Fill in the Blank): e.g.,
DangerZone FITB "<100>" "100"
- R/F (Right/False): e.g.,
-
Scoring Summary
- At the end of the quiz session:
-
SESSION END SUMMARY 00 22 59 -
This likely represents:- Elapsed time or start time
- Score achieved: 22
- Maximum possible score: 59
-
Additionally:
Q-Score Quiz = E-ShowScore! : S=12.32,16Indicates internal scoring metrics or percentiles.
-
Score Table Breakdown
- The summary at the bottom includes individual question-level results:
-
| Question | Score | Max Score | Locked | Tries Used | Max | |----------------|-------|-----------|--------|-------------|-----| | Assistance R/F | 1 | 1 | FALSE | 1 | 0 | | Helper MC | 1 | 1 | FALSE | 1 | 0 | | RescueTeam MC | 1 | 1 | FALSE | 1 | 0 |
"Locked: FALSE" implies the questions could be attempted multiple times, but "Tries used" was 1 for each.
🔍 Insights
- User Progression: Francis navigated the course sequentially, engaged with several question formats, and submitted answers.
- Scoring: The system logged not just the score but also metadata like whether a question was locked and how many attempts were used.
- Purpose: Likely used for performance tracking, certification, or auditing of course engagement.
Log File
Access Control Encryption Digital Signatures - Quiz
Click the Quiz link below to test your understanding of access control, encryption, and digital signatures.
Digital Signatures - Quiz
Digital Signatures - Quiz