Security Threats and Privacy Considerations for Internet Protocols
Privacy Considerations for Internet Protocols
The Internet Engineering Task Force (IETF) requires consideration of security threats, and has a process to threat model focused on their organizational needs. As of 2013, they sometimes require consideration of privacy threats. An informational RFC Privacy Consideration for Internet Protocols, outlines a set of security-privacy threats, a set of pure privacy threats, and offers a set of mitigations.
The combined security-privacy threats are as follows:
The combined security-privacy threats are as follows:
- Surveillance
- Stored data compromise
- Mis-attribution or intrusion (in the sense of unsolicited messages and denial-of-service attacks, rather than break-ins)
- Correlation
- Identification
- Secondary use
- Disclosure
- Exclusion
Security threats
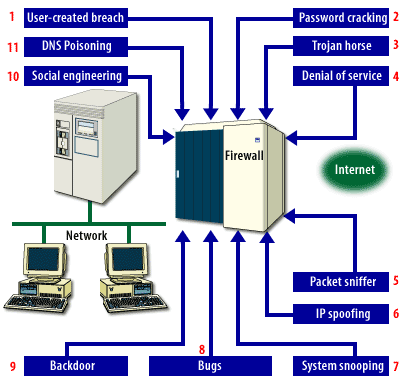
| 1) User-created breach | Users may unknowingly create a security risk by using weak passwords or by downloading a file containing a virus. |
| 2) Password cracking | Dictionary programs specifically written to break into a password-protected system are frequently used to gain access to network systems. |
| 3) Trojan horse | Users can inadvertently download destructive viruses and Trojan horses, thereby compromising a network's ability to function. A Trojan horse, or Trojan, is an illicit service that defeats authentication and access control measures. |
| 4) Denial of service | To prevent legitimate users of a service from using that service, attackers may attempt to flood a network or disrupt connections or services. |
| 5) Packet sniffer | Sniffers, devices, or programs that are used to monitor traffic on a network can be installed anywhere in a networked system. |
| 6) IP spoofing | Many hackers can imitate any Internet protocol (IP) device that has an address that allows them entrance into your system. |
| 7) System snooping | Using Transmission Control Protocol/Internet Protocol (TCP/IP), a hacker can enter a system through a device that does not have specific security mechanisms in place. |
| 8) Bugs | Many times, an operating system or program running on the server contains coding problems or bugs that create an unintentional opening. Hackers often know about such problems and exploit them. |
| 9) Back door | Program designers sometimes intentionally place a back door in an operating system or program so they can support the product quickly. Hackers can use the back door to gain access to the system. |
| 10) Social engineering | A hacker may use tricks and disinformation to gain access to passwords and other sensitive information. For example, a hacker might imitate a legitimate user by confusing a switchboard operator or a guard. |
| 11) DNS poisoning | It is possible for a hacker to misdirect users to other sites. For example, hackers can send bogus information to a DNS server that may make someone else's site appear as it were yours. |