| Lesson 8 | Reference architecture |
| Objective | Describe the value and significance of Published Reference Architectures |
Value and Significance of a Published Reference Architecture
In the realm of e-business, a "Published Reference Architecture" is a critical asset that provides substantial value and significance. This architecture serves as a blueprint or a guide, outlining the best practices, standards, and models for designing and implementing e-business systems. Its value and significance can be understood through several key aspects:
In conclusion, a Published Reference Architecture is a vital tool for organizations engaging in e-business. It serves as a comprehensive guide, helping businesses navigate the complexities of digital transformation, ensuring that their e-business systems are robust, efficient, and capable of adapting to the ever-changing digital landscape.
- Standardization and Best Practices: A Published Reference Architecture offers a standardized approach to designing e-business systems. By adhering to recognized best practices, it ensures that the systems are robust, scalable, and efficient. This standardization is particularly vital in an environment where technologies and business models evolve rapidly.
- Efficient System Design and Integration: With a reference architecture, businesses can design and integrate their e-business systems more efficiently. It provides a clear framework and guidelines, which helps in reducing the time and resources required for system development and integration. This is crucial in maintaining competitiveness in the fast-paced digital marketplace.
- Risk Mitigation: By following a proven architecture, businesses can significantly reduce the risks associated with implementing new technologies. The reference architecture has already addressed common challenges and pitfalls, ensuring that businesses do not have to navigate these issues from scratch.
- Facilitating Scalability and Flexibility: E-business environments require systems that are both scalable and flexible to adapt to changing market demands. A Published Reference Architecture provides a framework that supports scalability and flexibility, enabling businesses to grow and evolve their e-business operations without major overhauls of their IT infrastructure.
- Interoperability and Compatibility: In today’s interconnected business environment, e-business systems need to communicate and work seamlessly with other systems and technologies. A reference architecture ensures that new systems are built with interoperability in mind, facilitating smoother interactions between different technologies and platforms.
- Guidance for Compliance and Security: E-business systems must adhere to various regulations and standards, especially concerning data security and privacy. A Published Reference Architecture often incorporates these compliance requirements, providing guidance on how to build systems that meet legal and security standards.
- Knowledge Sharing and Industry Collaboration: A Published Reference Architecture, especially when it is the result of industry collaboration, represents a body of knowledge that is invaluable for the industry. It fosters a culture of sharing best practices and lessons learned, which benefits the entire e-business ecosystem.
In conclusion, a Published Reference Architecture is a vital tool for organizations engaging in e-business. It serves as a comprehensive guide, helping businesses navigate the complexities of digital transformation, ensuring that their e-business systems are robust, efficient, and capable of adapting to the ever-changing digital landscape.
Internetworking Models, Layering Protocols and OSI (7-Layer) model
People started thinking about frameworks when the monolithic, single-tier architecture of the mainframe started to die out in the mid-1980s. The rise of desktop computing and client-server architecture brought about a shift in thinking about technology, information and business processes. It was becoming apparent that separating these domains was resulting in dysfunctional systems that could not inter-operate. The (OSI model) Open Systems Interconnection model is a product of the Open Systems Interconnection effort at the International Organization for Standardization. It is a way of sub-dividing a communications system into smaller parts called layers. A layer is a collection of similar functions that provide services to the layer above it and receives services from the layer below it. On each layer, an instance provides services to the instances at the layer above and requests service from the layer below. For example, a layer that provides error-free communications across a network provides the path needed by applications above it, while it calls the next lower layer to send and receive packets that make up the contents of the path. Two instances at one layer are connected by a horizontal connection on that layer.
TCP/IP Models
The most widely known reference model is that of the Open Systems Interconnections (OSI), referred to commonly as the 7-layer model. It is most often compared directly to the transmission control protocol/Internet protocol (TCP/IP) model and we shall follow the same pattern in this module. For any model the concept of a service provider and receiver is used. Each standard divides the reference model into a number of layers, each of which acts as a service receiver or provider, depending upon the logical state it is in. The OSI reference model was produced by an ISO working group[1] and is occasionally referred to as the ISO model. It is the generic model for all networked systems although other protocol standards use a different number of layers. In the OSI 7-layer model the following layers are present: physical layer, data link layer, network layer, transport layer, session layer, presentation layer, and the application layer. It is common practice to use the numbers associated with these layers rather than their names. Therefore the physical layer is known as layer 1,
the data link layer is known as layer 2, the Network Layer is known as layer 3, and so on. These interact with their corresponding layers across the network on a peer-to-peer basis[2] so that each believes it has direct contact with its own peer layer. This is shown in Figure 1 for a single connection. The fact that each layer conceptually responds to its neighboring layer at the same level allows network connections to operate without the upper layers.
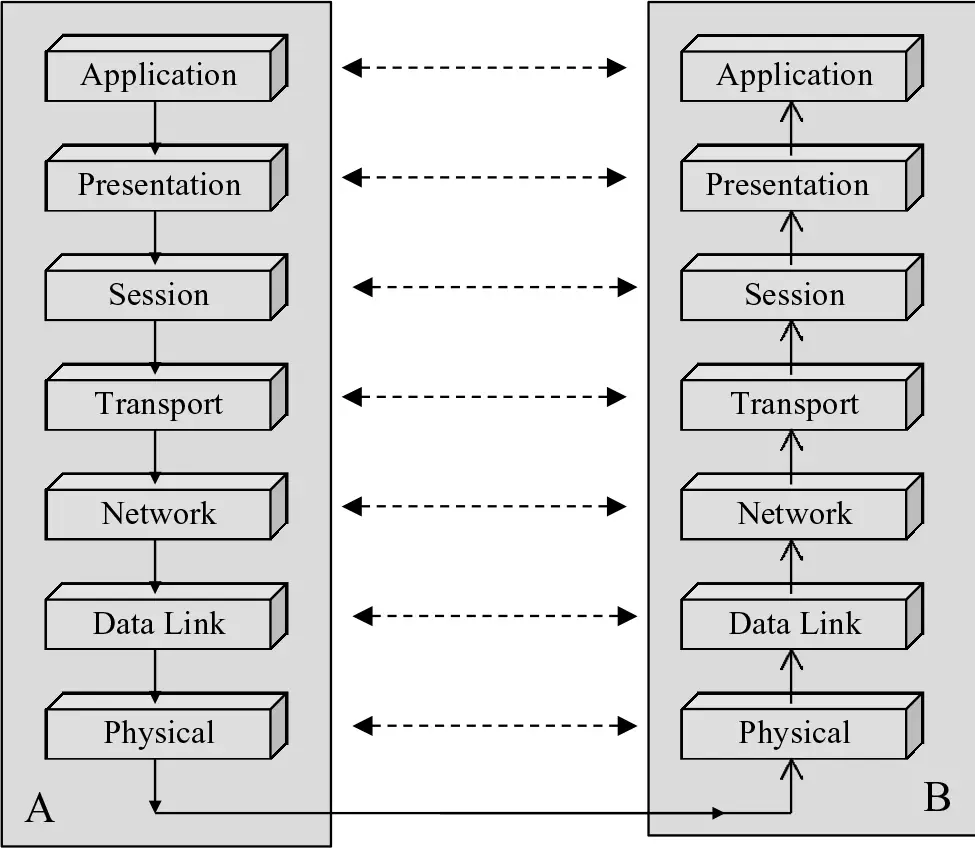
The physical layer (layer 1) defines the physical and electrical characteristics of a network interconnection. These are implemented in the wiring, the connectors, and the network interface cards of the hosts. The data link layer (layer 2) determines how the physical medium is accessed. HDLC, SLIP, and PPP protocols operate in part at this level. For the Ethernet MAC addresses are located at level 2 and this allows a LAN to become aware of its constituent members by their unique hardware addresses. The network layer (layer 3) allows systems using the same protocol to establish, maintain, and terminate connections.
The IP protoc*ol operates at the network layer, as do local hardware components such as routers. The transport layer (layer 4) ensures data reliability and integrity (TCP is usually considered to operate at this layer); retransmission requests and packet duplication problems are also resolved. The session layer (layer 5) has responsibility for ensuring sessions are completed without interference when necessary. This is important to e-commerce where the transaction cannot be disturbed by load sharing during its processing. The presentation layer (layer 6) deals with decryption, protocol conversion, and graphics expansion prior to presenting the information to the application layer. Layer 7, the application layer, is the part the user sees and uses.
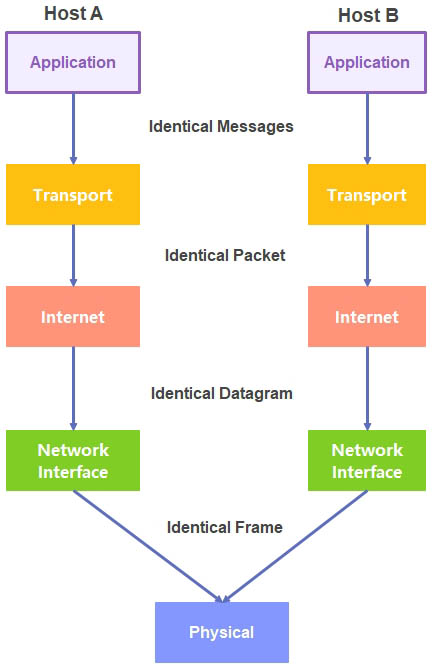
At this layer are applications such as FTP and other packages that require network access. The TCP/IP structure is similar and due to its earlier commercial support (and support from the DoD in the USA) is the de facto applied standard. (It should be noted that the Department of Defense did eventually formally move to the OSI model.) The structure is shown in Figure 8.2.
Reference architecture attempts to provide a standard process and representation for architects. There have been several attempts to develop reference models[3] in order to structure the architectural process and define the deliverables to be produced. There are almost as many frameworks for architecture as there are architects. KPMG has a framework embedded within the Enterprise Technical Architecture Methodology now incorporated into the Traction methodology. The competitors of KPMG have similar architecture frameworks differing only in terminology and glossiness of the graphics. Let us take a look at a few of these reference models to learn more.
Open Systems Interconnect (OSI) model
The results of the ISO efforts led to the publication of the OSI model in 1984.
The OSI model is now considered the primary conceptual model for inter-computer communications. The OSI model divides the problem of network communication between computers into seven smaller and more manageable layers, each layer specifying a particular network function.
The OSI model is now considered the primary conceptual model for inter-computer communications. The OSI model divides the problem of network communication between computers into seven smaller and more manageable layers, each layer specifying a particular network function.
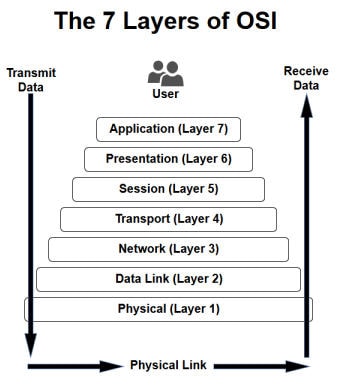
- Application Layer 7: OSI Model, Layer 7, supports application and end-user processes. Communication partners are identified, quality of service is identified, user authentication and privacy are considered, and any constraints on data syntax are identified. Everything at this layer is application-specific. This layer provides application services for file transfers, e-mail, and other network software services. Telnet and FTP are applications that exist entirely in the application level. Tiered application architectures are part of this layer. Layer 7 Application examples include WWW browsers, NFS, SNMP, Telnet, HTTP, FTP
- Presentation Layer 6: This layer provides independence from differences in data representation (e.g., encryption) by translating from application to network format, and vice versa. The presentation layer works to transform data into the form that the application layer can accept. This layer formats and encrypts data to be sent across a network, providing freedom from compatibility problems. It is sometimes called the syntax layer. Layer 6 Presentation examples include encryption, ASCII, EBCDIC, TIFF, GIF, PICT, JPEG, MPEG, MIDI.
- Session Layer 5: This layer establishes, manages and terminates connections between applications. The session layer sets up, coordinates, and terminates conversations, exchanges, and dialogues between the applications at each end. It deals with session and connection coordination. Layer 5 Session examples include NFS, NetBios names, RPC, SQL.
- Transport Layer 4: OSI Model, Layer 4, provides transparent transfer of data between end systems, or hosts, and is responsible for end-to-end error recovery and flow control. It ensures complete data transfer. Layer 4 Transport examples include SPX, TCP, UDP.
- Network Layer 3: Layer 3 provides switching and routing technologies, creating logical paths, known as virtual circuits, for transmitting data from node to node. Routing and forwarding are functions of this layer, as well as addressing, internetworking, error handling, congestion control and packet sequencing. Layer 3 Network examples include AppleTalk DDP, IP, IPX.
- Data Link Layer 2:At OSI Model, Layer 2, data packets are encoded and decoded into bits. It furnishes transmission protocol knowledge and management and handles errors in the physical layer, flow control and frame synchronization. The data link layer is divided into two sub layers: The Media Access Control (MAC) layer and the Logical Link Control (LLC) layer. The MAC sub layer controls how a computer on the network gains access to the data and permission to transmit it. The LLC layer controls frame synchronization, flow control and error checking. Layer 2 Data Link examples include PPP, FDDI, ATM, IEEE 802.5/ 802.2, IEEE 802.3/802.2, HDLC, Frame Relay.
- Physical Layer 1: OSI Model, Layer 1 conveys the bit stream - electrical impulse, light or radio signal through the network at the electrical and mechanical level. It provides the hardware means of sending and receiving data on a carrier, including defining cables, cards and physical aspects. Fast Ethernet, RS232, and ATM are protocols with physical layer components. Layer 1 Physical examples include Ethernet, FDDI, B8ZS, V.35, V.24, RJ45.
OSI Model and Zachman Framework
In 1978, the lack of interoperability between computers, combined with the growing desire for inter-computer communication, prompted the International Standards Organization (ISO) to standardize protocol creation.
One of the first reference models for developing architectures was the Zachman framework. John Zachman broke up the architecture space into perspectives (owner, builder, sub-contractor) and domain (data, function, network, etc.). In the graphic to the left each cell represents the artifacts produced in architecture engagement. With the advent of distributed computing and the development of the services concept, the Zachman framework underwent further morphing. Something similar to the "layer cake" was eventually adopted by most professionals for use in thinking about IT architecture.
One of the first reference models for developing architectures was the Zachman framework. John Zachman broke up the architecture space into perspectives (owner, builder, sub-contractor) and domain (data, function, network, etc.). In the graphic to the left each cell represents the artifacts produced in architecture engagement. With the advent of distributed computing and the development of the services concept, the Zachman framework underwent further morphing. Something similar to the "layer cake" was eventually adopted by most professionals for use in thinking about IT architecture.
E-business Architecture Cake Layer
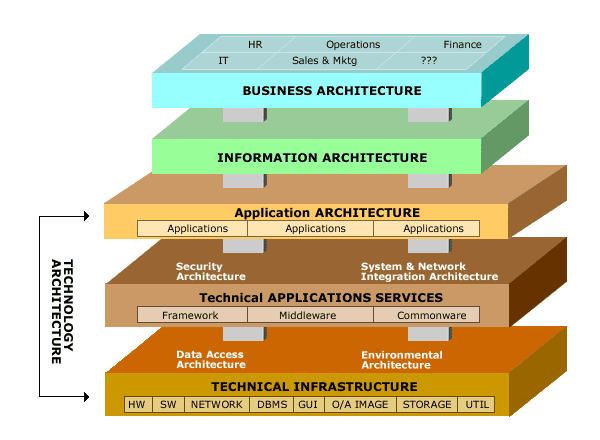
- Business Architecture
- Information Architecture
- Application Architecture
- Technical Applications Services
- Technical Infrastructure
Customize and extend the application functionality using abstraction layers, rather than in the application package itself.
The Layer Cake
This layer cake required a lot of slicing and dicing in order to view architecture from different stakeholder perspectives. While it was a useful framework for IT people to think about ERP systems and large-scale enterprise application portfolios, it did not necessarily make it "easy-to-do" architecture. Nor did it convey useful information to those stakeholders unfamiliar with the IT domain.
Conceptual, Logical, Physical
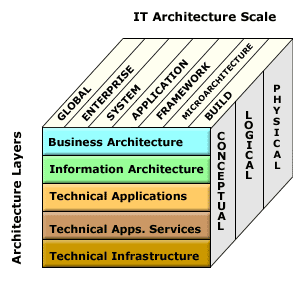
- Business Architecture
- Information Architecture
- Technical Applications
- Technical Apps Services
- Technical Infrastructure
The BIT Cube approach
The BIT cube represents architectural artifacts as bricks (or components) on specific topics that make up the cube. These artifacts are difficult to integrate as a continuous thread through the business, information and technology architecture views. This difficulty has made the BIT as separate architectural steps a less-favored approach. With the emergence of e-Business, separation of technology, information, and business architectures no longer makes sense. The architect's framework must enable the integration of these separate steps, automatically reconciling and aligning the requirements of various stakeholders (perspectives) across more natural partitions of the problem space (domains). You will learn more about architecture frameworks and the approach prescribed in this course. Namely, the module entitled the building blocks of architecture will introduce you to the concepts and approach prescribed by the authors of this course. Creating separate business, information, and technology architectures no longer works in e-space. There needs to be another way to think about architecture and represent the results of that thinking, in order to drive more quickly through the architectural process.
[1]
ISO Working Group:ISO standards are developed by a small group of experts representing participating countries in the ISO Technical Committee (TC) or Sub-Committee (SC). These experts represent their expertise on the subject matter and not their country as they discuss the finer points of terminology used, interpretation and technical aspects of the standard. They are the members of the Working Group (WG).
[2]
Peer-to-peer Basis: Peer-to-peer interaction describes an approach to interaction and collaboration
between participants in a shared project or activity that is characterized by networkbased organizational structures, a shared common resource base, and an assumption that all participants have the potential to make constructive contributions.
[3]
Reference models: Diagrams that are used for understanding. That is, people reference these models for the purpose of helping them make decisions or create an architecture.
Ad Advanced Digital Architectures