| Lesson 2 | Foundation technologies |
| Objective | Identify the network and security technologies required for eBusiness. |
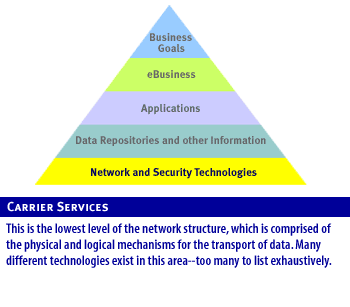
Foundation Technologies
Any eBusiness solution, whether B2B or B2C, must be based on a solid technology foundation. Network technologies, data, and applications form the base of the eBusiness pyramid.
- eBusiness is about using Technology:
It is easy to lose sight of the fact that eBusiness is about using technology to facilitate or enable business, and not simply about technology. For this reason, we're not going to try to cover these technologies in detail, or to concentrate heavily on any one type of technology. Although it is important for you as the architect to be aware of the technology and technology issues, you don't have to be a technology guru.- What we are going to do is draw your attention to the technological issues and questions to consider:
- Does this solution facilitate or get in the way of possible relationships with other vendors now and in the future?
- Is this technology compatible with other architectures?
- Can it be integrated with the applications that you now use?
- How easy is it to locate and use party resources?
Natural Evolution
Natural evolution is the process of optimizing the characteristics and architecture of human beings on earth. Possibly evolving the optimal characteristics and architectures of the living beings are the most complex problems being optimized on earth since the beginning of time. The evolutionary technique though it seems to be very slow is one of the most powerful tools for optimization, especially when all the existing traditional techniques fail. These evolutionary techniques can be used to generate optimal architecture and characteristics of different machine learning techniques. Mainly the two different types of networks considered in this module are
- artificial neural network and
- polynomial network.
Future Proofing your Business
As we discussed in a previous module with the issue of future proofing, the speed at which new technologies emerge in this area makes technology decisions obsolete in a very short time, regardless of how good they are. For this reason, it is important to utilize a standards-based technology[1] rather than proprietary systems[2] that could result in a technology dead-end, from which it is difficult and costly to recover. Where possible, it is often better for an organization to acquire technology and customize it than to develop it from scratch. As we discussed in an earlier lesson, these technologies may be provided internally (in-house) or by a technology partner (outsourced).
Foundation Technologies
Foundation technologies are focused on providing a secure, compatible, and manageable infrastructure and interface for the applications and data that make up the eBusiness solution. These technologies not only form the fundamental building blocks of the solution, but also provide the means by which the rest of the components interact. Let's briefly look at the two key subsystems of this foundation layer that must work in harmony to support the solution:
- Networks The network is the base technology; its purpose is to enable efficient and reliable communication between host-end systems and between host and client-end systems. The network can be subdivided into the following components:
Network Components

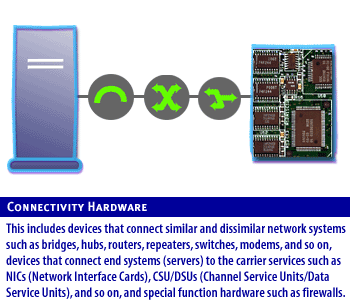
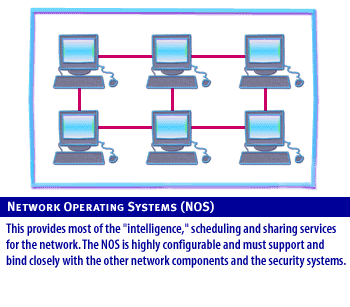
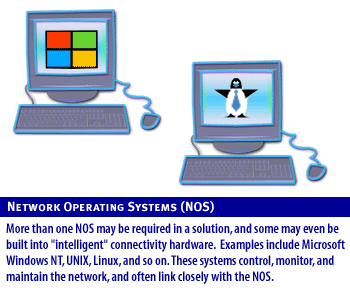
Examples include Microsoft Windows Unix and Linux. These systems control, monitor and maintain the network and often closely with the network operating system.
Network Layer Choices
Some of the factors that will influence your choices in the network layer are as follows:
- Application requirements: The Application requirements are of prime importance. The solution should not be built around the network layer. Rather, the network layer should be chosen to support the application.
- External connectivity: Does the application require connectivity to a wide variety of client-end devices and applications? Where are the customer's located? What is the total and simultaneous user count expected to be?
- Internal connectivity: In some cases, legacy systems in the organization may dictate these choices.
- Bandwidth: The types and quantities of data movement and the number and type of connections both internally and externally set the minimum bandwidth requirements. Physical constraints or monetary constraints may determine maximum bandwidth.
- Skills and expertise: In some cases, the costs of finding and retaining the necessary expertise to implement and maintain the desired network infrastructure may prove prohibitively costly.
- Security: The job of the network subsystem is to allow users to connect to the eBusiness systems. The security subsystems control and even prevent some users from accessing the network subsystem. As was mentioned in an earlier module, the architect's responsibility is to know the security chinks in the site's armor. Security protects the company's resources, and can be either physical (hardware), logical (software), or a combination of both.
- Security subsystems: Security subsystems have to be balanced to ensure they are strong enough to provide the appropriate levels of security without interfering with the running of the applications or the maintenance and upkeep of the system.
B2B Digital Marketing Strategy
Tasks of the Security Subsystem
| Function | Description |
| Authenticate and authorize | Identify who is accessing the system Determine and control the levels of access to resources based on a set of permissions |
| Control Integrity | Ensure the data is transmitted intact to the intended recipient without being intercepted |
| Audit | Monitor and log the activities of connected users and system events |
- Directory Services
Security systems may utilize advanced Directory Services to centrally maintain information for and about the resources, such as users, shared facilities, applications, and policies. Directory Services allow a single network logon to a system that can then be centrally maintained. Lightweight Directory Access Protocol (LDAP)[3] is a common technology for implementing Directory Services.
In the next lesson, we will discuss the use of a database in an eBusiness context.
Foundations of Educational Technology
Foundation Technologies - Quiz
Click the Quiz link below to complete a quiz on foundation technologies.Foundation Technologies - Quiz
[1]Standards-based technology: Technology based on Open Systems standards. B2C: A primary two-business model where the seller is a business and the buyer is a consumer or individual such as with a bookstore that sells books to the public.
[2]Proprietary systems: Proprietary is the opposite of open. A proprietary design or technique is one that is owned by a company. It also implies that the company has not divulged specifications that would allow other companies to duplicate the product.
[3]Lightweight Directory Access Protocol (LDAP): Lightweight Directory Access Protocol, a set of protocols for accessing information directories. LDAP is based on the standards contained within the X.500 standard, but is significantly simpler. And unlike X.500, LDAP supports TCP/IP, which is necessary for any type of Internet access. Because it is a simpler version of X.500, LDAP is sometimes called X.500-lite.
Although not yet widely implemented, LDAP should eventually make it possible for almost any application running on virtually any computer platform to obtain directory information, such as email addresses and public keys. Because LDAP is an open protocol, applications need not worry about the type of server hosting the directory.
Although not yet widely implemented, LDAP should eventually make it possible for almost any application running on virtually any computer platform to obtain directory information, such as email addresses and public keys. Because LDAP is an open protocol, applications need not worry about the type of server hosting the directory.