| Lesson 3 | In-house or outsourced solutions |
| Objective | Describe the advantages and disadvantages of in-house Development and Hosting |
How to move to e-business
Once you have answered the important "if," why," and "when" questions concerning the move to eBusiness, the next important question to tackle is "how."
We will examine the planning and implementation phases of development in greater detail later in the course. However, in moving to an eBusiness solution, part of the "how" question is actually a question of "who." When you are deciding who will implement the solution, you have several paths from which to choose. You can stay within the organization and create an eBusiness group. A second alternative is to collaborate with a technology and/or integration partner, or to create an eBusiness subsidiary. A third solution might be a hybrid of the first two routes. No matter your approach, there are some global questions you must consider. You must consider a number of factors to determine who will implement the solution. To make this implementation choice, you should assess four factors, which are described in the Easy Reference below.
Questions to Consider in deciding who will implement your e-business
These factors pose some important questions. Let's consider both the in-house and the outsourcing solutions in detail. The in-house solutions are reviewed in the series of images below.
Questions to Consider in deciding who will implement your e-business
| Factor | Questions to consider |
| Projected immediate and long-term costs | What is the cost of establishing an in-house solution compared to the cost of hiring an external team? |
| Required service levels | Can the organization handle the service levels needed for the in-house solution, such as twenty-four-hours-a-day, seven-days-a-week support? |
| Time to market | Does the infrastructure already exist? If you have to build the infrastructure first, the solution will be longer in the making. |
| Anticipated response times for changes | Does the external partner see the changes and future enhancements with the same level of urgency? |
| Vendor lock-in | What are the costs of being locked-in to a specific software platform? Outsourcing can lock you into thechosen software platform of the external partner. If you decide to move elsewhere or take the function over in-house, it could be difficult and expensive to change software platforms. |
| Accountability | Who will be responsible for monitoring potential challenges and for assigning financial liability shouldproblems arise? The more parties involved in a solution, the more difficult it is to assign accountability for fixing potential problems. In some cases, a fault in an area controlled by one technology partner may lead to additional problems developing in another. It can then become difficult to identify who is financially responsible for fixing the problem. |
These factors pose some important questions. Let's consider both the in-house and the outsourcing solutions in detail. The in-house solutions are reviewed in the series of images below.
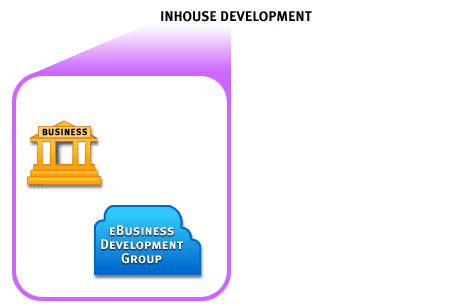
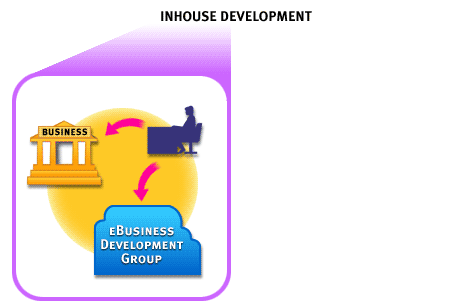
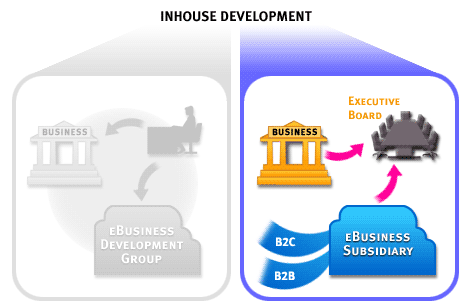
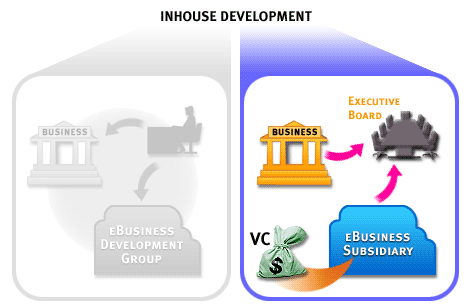
Note that in a bid to gain control over the ebusiness function by creating it entirely in-house, an organization risks of losing the race to keep up with fast-paced changes in technology.
An Outsourced Solution
If you use an outsourced development and hosting solution, an external integration partner manages the business. These outside agencies are also known as Application Service Providers. [1] The fast-paced changes in the e-business world have given rise to a number of Application Service Providers. In fact, DistributedNetworks is an example of an Application Service Provider.
- Finding the right e-business partner: Finding the appropriate partner is critical to the success of any e-business venture. A technology partner will provide the business with the technical foundation for your e-business. This will include the hardware infrastructure[2] and connectivity resources[3] and may be wholly or partially located or hosted in a physically remote site. Contractual agreements can specify minimum acceptable transaction throughput[4] times and bandwidth[5] availability. In agreements for co-location (also known as colo), an organization physically hosts a company's equipment in the co-location's secure environment. The company may still control and maintain the server, but use the co-location facilities to ensure the safety and security of their server. Your responsibility as the architect, is to know your site's vulnerabilities.
Safeguarding your Website against Unauthorized Entry
Security is an extremely diverse and complex topic. As an architect, your focus should be on considering security implications at every step in preparing the business for e-business, and in an ongoing effort to raise awareness within the enterprise, as well as with your customers. There are four steps to safeguard your site against unauthorized entry :
- Be explicit in educating their consumers on their products' security risks.
- Educate your employees on the preventative and defensive tools available for denial-of-service and other cyber attacks.
- Accept the fact that many websites have been tampered with; a willingness to share your experiences and solutions with others, even competitors, is a long term investment in addressing the problem.
- Insure the OS of your server is up to date: Often the operating system of your webserver may have several issues and could potentially have security vulnerabilities that can leave your server open to attacks that compromise your computer and your data. Software patches and updates are made available to clients to help keep a software program and operating system running properly and secure. If the program you are using does not have any method of checking for updates on its own it is up to you to verify the program is up-to-date. Often this can be done by visiting the website of the developer who created the program. A listing of third-party companies and links to each of their pages can be found on our third-party support page.
- Convenience versus Security: What we have witnessed was a surprisingly rapid and efficient transition. Just a couple of years ago, the Web used to function as an unassuming tool to deliver predominantly static, externally generated content to those who searched for it. However, this is no longer the case. We live in a world where the very same old-fashioned technology now serves as a method to deliver complex, highly responsive, dynamic user interfaces. In addition, the functionality was previously restricted to desktop software. The evolution of the Web is both exciting and frightening. Along with the unprecedented advances in the offered functionality, we see a dramatic escalation of the decades-old arms race between 1) developers who write the code and 2) testers those who try and break it.
This is not a glorious war of black and white hats, and for the most part, there is no good versus evil. It is a mundane clash we are dealing with here, one between convenience and security. Those of us working in the security industry must take sides for both of the opposing factions to strike a volatile and tricky compromise. There is no end to this futile effort and no easy solutions on the horizon.
Application Service Provider and Co-location Facility
An example of an Application Service Provider would include a co-location facility that provides complex Internet hosting for enterprises with mission-critical Internet operations. A colocation center is a type of data centre where equipment, space, and bandwidth are available for rental to retail customers.
Colocation facilities provide space, power, cooling, and physical security for the server, storage, and networking equipment of other firms and connect them to a variety of telecommunications and network service providers, with a minimum of cost and complexity. Colocation has become a popular option for companies with midsize IT needs since it allows the company to focus its IT staff on the actual work being done, instead of the logistical support needs which underlie the work.
Significant benefits of scale result in large colocation facilities, typically 4500 to 9500 square meters.
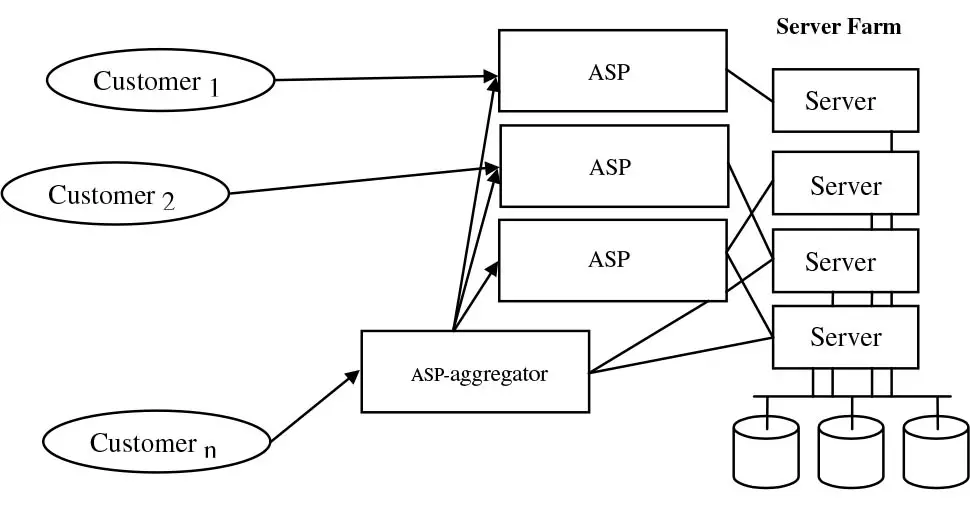
- Application Service Providers: Application service providers are third-party entities that manage, deploy, and host software-based services and applications for their customers from server farms and datacenters across wide area networks. Customers access the hosted application remotely and pay in a subscriptionbased manner. In essence, ASPs constitute a way for companies to outsource some or all aspects of their information technology operations, thus dramatically reducing their spending in this area. Services and applications offered by ASPs may be broadly categorized as follows:
- Enterprise application ASPs: Enterprise application ASPs deliver high-end business applications, such as enterprise resource planning solutions. Customers are corporate clients who need these solutions but want to avoid investing in proper in-house installations. Locally constrained ASPs deliver a wide variety of (mostly bundled) application services in a local area, such as a portal for all the shops in a city or tourist information services for a region, including event registration, booking, and ordering features. These serve both the individual users as well as the local entity (e.g., shop or museum).
- Specialized ASPs: Specialized ASPs deliver highly specialized applications addressing one specific function, such as news, sports and stock tickers, weather information or credit card validation. Customers are usually other online service providers who bundle multiple services.
- Vertical market ASPs: Vertical market ASPs deliver applications catering to one specific industry, such as insurances, human resource management, media asset management or health care. The customer is the corporate client.
- Bulk-service ASPs: Bulk-service ASPs deliver applications for businesses in large quantities, such as e-mail, online catalog, document, or storage management.
- ASP aggregators: ASP aggregators combine the offerings of several ASPs and provide the user with service bundles and a single way to interact with all the aggregated ASPs.
ecommerce Business Model
The Role of the Integration Partner
An integration partner develops and/or integrates the software application. The business and integration partner need to work closely on the development of the software application. The solution may involve interfacing to existing legacy information systems[6] and will certainly involve interfaces to existing business functions. These interfaces need to be monitored and maintained in-house.
- The hybrid solution: It is also possible to consider a mixed development and hosting solution. An external team could develop and implement the solution and then rent it to or hand it over to, the business. We will consider the options of building, buying, and renting the solution in another module. The following section discusses In-House Versus Outsourced Development.
In House versus outsourced Development and Hosting
- An e-business group: A strongly controlled extension of the existing business and product/service mix
- Application Service Provider: An external integration partner
- Time to market: One of four factors to be considered in deciding who will implement the solution
- An e-business subsidiary: A way of establishing an in-house e-business presence more quickly
- A mixed development and hosting solution: An outside team develops and implements the solution and then rents it to the business
- Legacy information system: An existing hardware and/or software system to which a new e-business solution must interface
Now that so many senior executives are learning the power of e-business-architecture, the demand for qualified in-house e-business (full time or contract employees) has grown by leaps and bounds. This is similar to other business needs that were first identified and controlled by the domain of outsourced consultants, such as high-profile headhunting (recruiting), or applications development projects, for example. The relationship between in-house and agency e-business-architecture experts has never really been an adversarial one. Over the years, people have evangelized the merits of one over the other in forums and in blogs, as well as within organizational marketing planning and strategy meetings. In my opinion, the ideal strategy is to get the best of both worlds. One should hire the best possible internal staff, but also solicit the support of a e-business-architecture firm in order to get the most out of Internet marketing efforts. The trick is finding the right level of skill on both sides, and avoiding the creation of conflict between the parties. If the in-house team or manager can work well with the agency, and goals are being met. Should competition take over, then needless time will be wasted, derailing the marketing efforts behind everything.
In the next lesson, we will describe the importance and sequence of training staff and users.
[1] Application Service Provider: Application Service Providers are third-party entities that host (manage and distribute) software-based services and solutions to customers across a wide area network from a central data center. Do not confuse this acronym with Active Server Pages (ASP). ASP is a form of applications outsourcing.
[2]Hardware infrastructure: Servers, disk arrays and other storage devices, power supply and protection devices and physical communications devices.
[3]Connectivity resources: Connectivity resources refer to the network infrastructure required to connect a computer and its contents to other computers. This includes physical devices like modems, switches, hubs, routers, bridges, cabling and satellite links as well as network protocols, operating systems and security systems.
[4]Transaction throughput: The number of transactions than can take place in a period of time.
[5]Bandwidth: The amount of data that can be transmitted in a fixed amount of time. For digital devices, the bandwidth is usually expressed in bits per second(bps) or bytes per second.
[6] Legacy information systems: Legacy information systems refer to older software or hardware systems that are still in use, often crucial to an organization's operations. They are typically characterized by outdated technologies, rigid architectures, and challenges in integration with modern systems.