| Lesson 6 | Fending off an attack |
| Objective | Define encryption types that are used to fend off attacks. |
Fending off DOS Attack
You have implemented a cryptosystem to protect your ecommerce site, but you may want to ensure that the site remains secure from even the most sophisticated hackers. Though many vendors offer techniques that can dissuade even though most sinister hacker, you should have a basic understanding of what those techniques are; this lesson provides you with that overview.
- How to fend off attack How do you fend off these various forms of attack?
Different "strengths" of encryption provide the means to foil attempted security breaches. A commonly discussed but frequently misunderstood aspect of cryptography is the strength of encryption.
What constitutes "strong encryption," which is protected by U.S. export laws?
What level of encryption is required for various security needs? How do you determine the effective strength of different types of encryption?
These questions are addressed below. - Encryption types
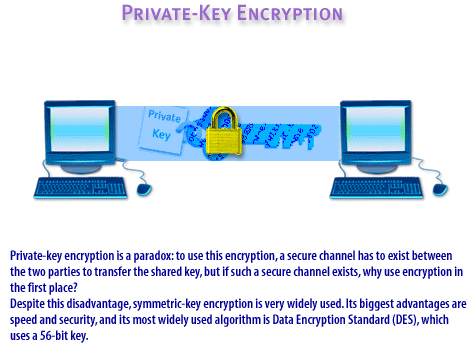
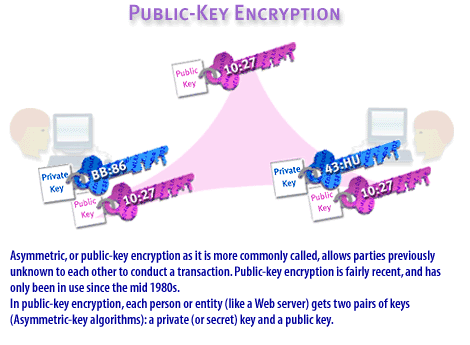
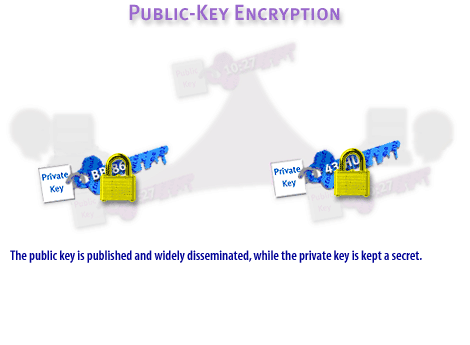
Finally, there are three basic encryption types, which typically vary based on how they use keys. The three encryption types include private or symmetric encryption, public or asymmetric encryption, and one-way encryption. They are described in the FlipBook below. A private key might be compared to your house key, and a public key likened to your house number. You give access to the first only to those you know and trust. The second is publicly available information.
Secure ecommerce Transactions
Types of Encryption
- Main Points :
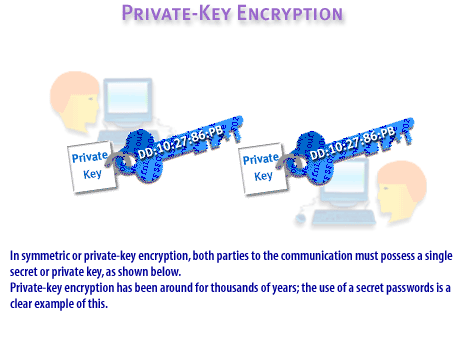
- Title: Private-Key Encryption
- Description: "In symmetric or private-key encryption, both parties to the communication must possess a single secret or private key, as shown below. Private-key encryption has been around for thousands of years; the use of a secret password is a clear example of this."
- Relevant Features:
- Visual Representation: The image depicts two people at computers (likely representing two parties in communication). Both of them hold the same key labeled "Private Key" with identical information ("DD:10:27:86:P8"). This symbolizes symmetric encryption, where both parties use the same key for encryption and decryption.
- Key Concept: The image is illustrating private-key (symmetric) encryption, emphasizing that both the sender and the recipient need to have the same secret key to exchange encrypted information securely.
- Text Emphasis: The title is in larger, prominent text ("Private-Key Encryption"), suggesting that the image is focused on explaining the concept of symmetric encryption. The description emphasizes the history of private-key encryption and how passwords are an early example of this technique.
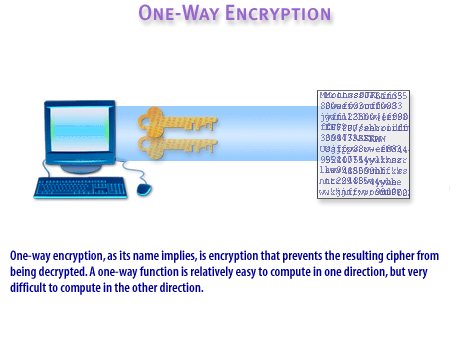
Nature of One-Way Encryption:
-
Hashing Concept:
- One-way encryption converts plain text (such as a password or PIN) into a hash value.
- The resulting hash is unique to the input data and cannot be reversed to obtain the original input.
-
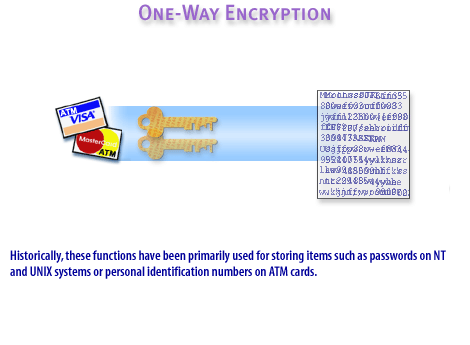
Usage Examples:
- The image suggests applications in storing passwords on NT and UNIX systems.
- It also mentions securing personal identification numbers (PINs) on ATM cards.
-
Irreversible Process:
- Unlike traditional encryption, which allows decryption using a key, one-way encryption does not have a "decryption" process.
- Instead, verification is done by rehashing the input and comparing it with the stored hash.
-
Security Considerations:
- One-way encryption is resistant to direct reversal.
- However, weak hashing algorithms may be vulnerable to attacks like rainbow table attacks or brute force attacks.
- Strong cryptographic hashing functions like SHA-256, bcrypt, or Argon2 enhance security.
Conclusion: The image conveys how hashing is used for security, especially for **password storage and authentication systems**. Since one-way encryption is irreversible, authentication relies on comparing the hashes rather than decrypting the stored values. 7) Historically these functions have been used for storing items such as passwords on Windows and Unix systems.
Encryption Technology
Encryption Strength
Encryption strength is based on three primary factors:
- Strength of the algorithm (or encryption procedure) Algorithm strength determines how difficult it is to mathematically reverse the encrypted information. The strongest algorithms make it nearly impossible to reverse the information with anything short of a brute force attack.
- Secrecy of the key: The second factor, the secrecy of the key, is a logical but sometimes overlooked factor in encryption strength. No algorithm, however strong, can protect you from compromised keys. Thus, the safety of your encrypted data is directly tied to how secret the key remains.
- Length of key: In terms of encryption and decryption formula application, the key length is determined in bits. Adding a bit to the length of the key does not increase its possibilities by two but, rather, doubles them.
Key length combinations and key strength
In simple terms, the number of possible combinations of bits that can make up a key of any given length can be expressed as 2 raised to the n, where n is the length of the key. Thus, a formula with a 40-bit key length would be 240, or 1,099,511,627,776 possible different keys. In general, keys with more bits offer stronger encryption than keys with fewer bits. No matter how many bits a key contains, it can always be broken, given enough time and computing power. The key length chosen should be directly proportional to the data being protected:
the more confidential the data, the higher the number of bits in the key should be. Working against us is the speed of modern computers. Although the number of possible keys is indeed large, specialized computers can now try that many combinations of keys in less than a day. Ron Rivest has explained cryptographic strength determined on the basis of key length, given the current state of computing power.
In the next lesson, you will learn about authentication.
In the next lesson, you will learn about authentication.